Configure the Textkernel Portal Configuration Custom Metadata Type
To complete the configuration of the TextKernel![]() A Bullhorn Recruitment Cloud partner. One of the Search and Match / Resume Parsin services providers integrated with Bullhorn Recruitment Cloud Portal Configuration Custom Metadata Type, you need a few values from your Portal Account.
A Bullhorn Recruitment Cloud partner. One of the Search and Match / Resume Parsin services providers integrated with Bullhorn Recruitment Cloud Portal Configuration Custom Metadata Type, you need a few values from your Portal Account.
Contact and provide the following information:
- JWT Issuer
- Portal Account Name. The Portal account name is always the same as the Candidate
 A person looking for a job. A candidate can also be referred to as a Job Seeker, Applicant, or Provider. Search environment name without the '_cv' .
A person looking for a job. A candidate can also be referred to as a Job Seeker, Applicant, or Provider. Search environment name without the '_cv' .
will provide back the following:
- URL
- Account name (Configuration Service Username)
- Admin password (Configuration Service Password)
All Textkernel Search and Match setup procedures are available here.
Steps
- Go to Setup > Custom Metadata Types > Textkernel Portal Configuration.
- Click the Manage Textkernel Portal Configurations button.
- Click on New.
- Fill in all the required fields following the instructions below. Save after entering all the information.
Required Fields Instructions
Label
Enter in any name, such as Portal Config.
Textkernel Portal Configuration Name
This will be automatically populated after entering a label.
Login URL
will provide this when Portal Account is created. The URL must be completed by adding sso![]() Single Sign On is an authentication process that allows a user to access multiple applications with one set of login credentials./jwt/login?jwt=
Single Sign On is an authentication process that allows a user to access multiple applications with one set of login credentials./jwt/login?jwt=
For example, if provides https://staging.textkernel.nl/tkportal/ then the correct Login URL will be: https://staging.textkernel.nl/tkportal/sso/jwt/login?jwt=
Signing Certificate Name
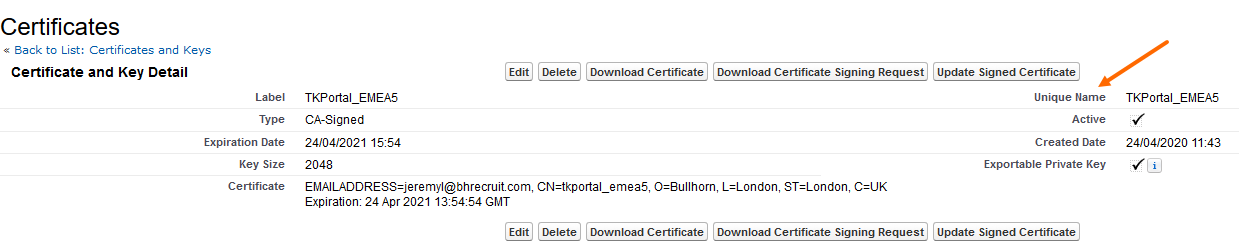
Copy this from Setup > Security > Certificate and Key Management and click on the name to open the record and copy the value in the Unique Name field.
Account Name
will provide this when the Portal Account is created.
JWT Issuer
This is entered in the format [CN value from Certificate record] : Bullhorn Recruitment Cloud Partner Services Intermediate CA.
A colon must be used to separate the two parts, the second part is always the same. The first part comes from the Certificate record:
- Go to Setup > Security > Certificate and Key Management.
- Select your certificate in the Certificates section.
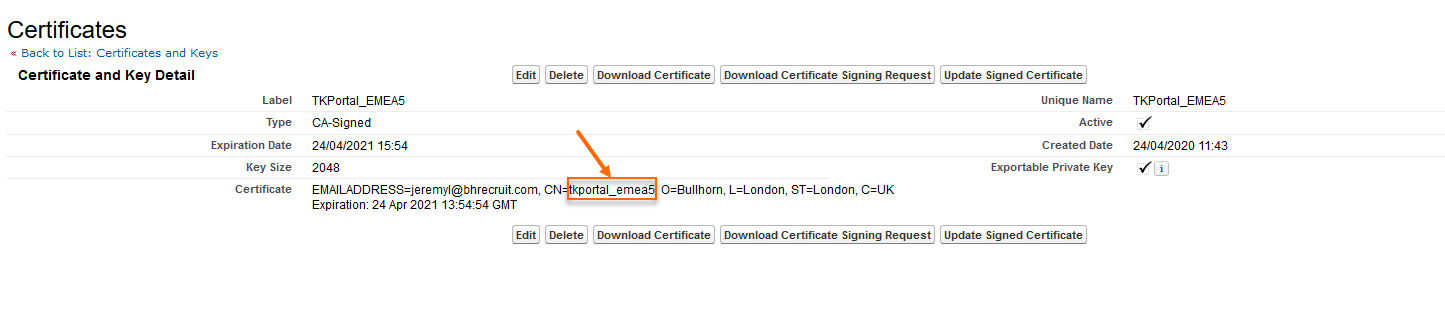
- On the Certificate record, go to the Certificate field and copy the string just after CN=.
The correct JWT Issuer value based on the screenshot above would be tkportal_emea5:Bullhorn Recruitment Cloud Partner Services Intermediate CA.
Signing Certificate
Open the .crt file of the signing certificate with any text editor. Copy all the text content between the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- lines and paste it into the Signing Certificate field.
Intermediate Certificate
Repeat steps above for Signing Certificate except with the Intermediate certificate provided by Bullhorn. Paste the text into the Intermediate Certificate field.
Root Certificate
Repeat steps above for Signing Certificate except with the Root certificate provided by Bullhorn. Paste the text into the Root Certificate field.
Configuration Service Username
This is the Account name will provide when the Portal Account is created.
Configuration Service Password
This is the Admin Password will provide when the Portal Account is created.
Search Policy URL
Bullhorn will provide the Service Endpoint![]() When two systems integrate, an endpoint is one end of a communication channel. URL.
When two systems integrate, an endpoint is one end of a communication channel. URL.
Use this format:
Prod Environment![]() In Salesforce terminology, any type of instance where the application can be used, like a production instance (where users use the product daily) or a testing environment (a Salesforce instance created just to develop and test features). Or can be used with reference to an external database: Service Endpoint URL + /portal/config/searchPolicy
In Salesforce terminology, any type of instance where the application can be used, like a production instance (where users use the product daily) or a testing environment (a Salesforce instance created just to develop and test features). Or can be used with reference to an external database: Service Endpoint URL + /portal/config/searchPolicy
UAT Environment: Service Endpoint URL + /tkportal/config/searchPolicy
User Config URL
Bullhorn will provide the Service Endpoint URL.
Prod Environment: Service Endpoint URL + /portal/config/user
UAT Environment: Service Endpoint URL + /tkportal/config/user